The healthcare industry has undergone a profound transformation thanks to the implementation of technology into its core operations. While daily administrative processes are now streamlined, these tec…
Wowrack Blog
secure network
Stay ahead in the world of IT with Wowrack's insightful news, tips, and blog. Explore expert perspectives, industry trends, and valuable insights to accelerate your digital transformation and business success!
Start NowFeatured Articles
Wowrack secure network Blog

Hybrid Cloud Best Practices
A hybrid cloud is like a computer environment that combines two types of clouds: a public cloud where many users share the resources, and a private cloud that is designated for just one organization. …
What is Security Posture?
Security posture refers to a company’s readiness for cyber security challenges. Evaluating a company’s security posture means checking the company’s policies, software, hardware, and networks.
…

Easy Minecraft Server Set Up
Setting up a Minecraft server is a great entry to understanding basic networking from a young age. Since the release of its first playable version on May 17th, 2009, Minecraft has become one of the mo…

Password Policy Best Practices
Another 90 days have come and gone, and then you see an all too familiar security message “It’s been 90 days since you’ve changed your password”. Annoyed, you sigh and go through process of c…
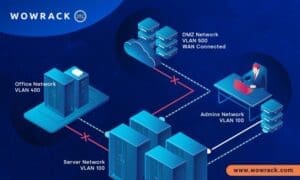
Building a Secure Network and Why it Matters
Having a secure network is something everyone needs for both personal or professional use. It prevents attackers from accessing important information and acquiring access to your system.
What…
Get a Free Consultation for Your Business
US Headquarter
12201 Tukwila International Blvd #100,
Tukwila, Washington 98168
United States of America
+1-866-883-8808
Tukwila, Washington 98168
United States of America
+1-866-883-8808
APAC Headquarter
Get Our Latest Updates and News
© 2024 Wowrack and its affiliates. All rights reserved.








